Google Chrome is a great web browser, but like with anything else in life, there are risks associated with using it. This blog post will discuss tips to help you
DDoS Update: Something Old, Something New
Distributed denial of service (DDoS) attacks are in the news again. Long-term DDoS trends continue their upward spiral, and RDDoS, a mashup of DDoS attacks and extortion threats, become a
Why Are Big Travel Companies a Target for Hackers?
Hackers are more than happy to target a wide range of different companies from all manner of sectors and industries, but travel companies have become a particular focus in recent
Why Cyber Security is Essential
Cybersecurity incidents are always on the rise. Both large and small organizations fall victim to cyber-attacks which are becoming more sophisticated. Using artificial intelligence (AI), attackers have tools that can
Is the Dark Web Dangerous and What Are the Legal Risks?
The dark web used to be a place for hackers, law enforcement agents, and all manner of cybercriminals, but in 2021 it’s possible for anyone to try it out. But
The Risks of Poor Database Security
A recent study found billions of records exposed in unsecured Elasticsearch and MongoDB libraries. These 10.5 billion pieces of consumer data reportedly included passwords, phone numbers, and email addresses. Three
Outdated IT Is The Biggest Cause Of Business Downtime, Not Hackers
We tend to think of downtime as something that happens when a hacker figures out how to compromise company systems. And while this is a risk, the biggest threat is
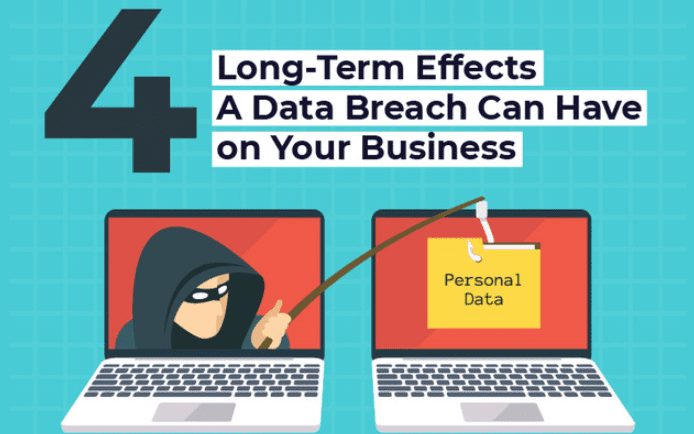
What Are The Long-Term Effects of a Data Breach? [INFOGRAPHIC]
Cyberattacks are becoming increasingly common day-by-day as hackers find new ways to circumvent companies’ security protocols and gain access to their data. Companies need to be more aware today and