Scaling to hundreds of services is much easier and efficient for cloud-native applications.
______________________________________________________________________________
We live in a cloud-native environment. The technologies and techniques that were effective before the cloud age, no longer function. This is unquestionably accurate in the case of confidential management.
Continue reading to know what the cloud-native transition entails for secrets and how companies should adjust their secrets management techniques to cloud-native environments such as CloudEnv.
What is a Cloud-native Environment?
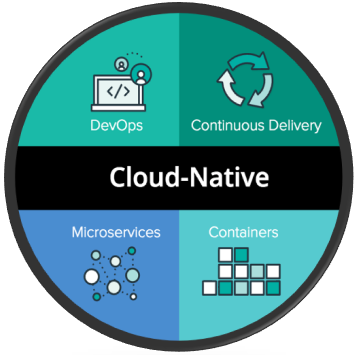
We sometimes dislike the phrase cloud-native because it does not have a very particular meaning, except in software motto standards. Ask several people what the native cloud entails different responses would be provided. For some, the word for anything running in the cloud is essentially a common one.
Whereas cloud-native is described as an IT Technique and Includes:
- Pace and scalability of implementation and upgrade are the main focus of the continuous supply of software applications.
- Flexible, modular systems, mostly focused on the design of microservices.
- Software-defined architecture that rapidly evolves, with servers, containers, and other ingredients spinning up and down.
- Software-defined architecture that rapidly evolves, with servers, containers, and other ingredients spinning up and down.
Control Problems with Cloud-native Secrets

Hidden management techniques built in several forms before the cloud-native period that do not fit in cloud-native environments. This is because:
Automation of Secrets Management
It is simple enough to maintain secrets by hand if apps are used as monoliths of static on-site services. Static addresses and hostnames. Few if no APIs exist, but you have to concern yourself only with passwords, not with other secrets. And less moving parts generally issue authentication and approval requests inside the environment.
That being said, it is not the case in cloud-native environments. Many more secrets have to be managed. There is regular variation in the addresses of the utilities and technology elements and the secrets with them.
For these purposes, highly automated secret management is important in cloud-native environments. Suppose your environment contains a variety of microservices on hundreds of containers through a wide range of servers. In that case, you can’t handle and exchange secrets by hand. Rather you must be willing, to simplify the approach secrets are kept and exchanged, to customize secret management policy in code.
Secrets of all Sorts Must be Managed
Most of the secrets were passwords until the cloud-native transition. While you may have had any encryption keys throughout the process, API tokens are rarer since the linking networks have not been integral to APIs.
However, various forms of secrets are continuously used in cloud-native worlds. It is not just people connecting to networks with names and passwords that rely on secrets; apps may even authenticate and approve keys and tokens. Consequently, personal management tools and procedures must be able to support all types of secrets from one place. For this function, password managers and network security services are not enough.

Centralization of Classified Information
Cloud-native ecosystems can be replicated by design through different infrastructures. It’s hard to monitor all the software and infrastructure components in this design. You don’t want to scatter your secrets thinly across a number of places either.
Instead, the administration of cloud-native secrets has to be centralized. Both secrets can be kept in one location with the organization. Classified centralization facilitates the implementation of best secret management compliance techniques. It also lets you monitor secret information from a central viewpoint, which is essential to abuse secrets through attackers or users who clearly do not obey guiding principles.
Select the Appropriate Apps
Some applications are more suited to cloud-native development than others. Suppose a company has minimized its security with low-risk applications. Then, it must find and prioritize the cloud-native apps that can have the maximum benefit. The one form of application that gains the most from cloud-native development is stateless applications.
Stateless apps comprise the majority of web-based applications that are easily accessible to end-users from the public internet. This form of software sees steady growth and decline in consumption. Scaling a cloud-native app is significantly simpler than scaling a legacy app. Therefore, stateless web-facing applications profit greatly from being cloud-native. Additionally, these are very simple to construct as cloud-native applications.

Incorporate All Teams and Adopt a Collaborative Attitude
Several teams must be involved to successfully execute a method as complex as a cloud-native environment. The organization’s developer departments must be included. Additionally, all teams should be on the same wavelength at all times and capable of collaboration and transparent communication. Some companies believe they only want developer teams to accelerate the adoption of cloud-native apps. But they wind up with insecure, underperforming cloud-native applications if they can make it that far.
Additional Considerations for SaaS Vendors
If a company offers SaaS software, there need to be a few additional boxes that must be checked to refer to their SaaS applications as comfortably cloud-native. For starters, every full cloud-native application can leverage the REST API. Additionally, any cloud-native application should be conveniently scalable to ten or more customers, implying that it should operate on any platform or browser. Finally, cloud-native applications must be able to switch freely across cloud platforms, preventing users from being tied to a single network.
Conclusion

A modern approach to remote management is needed to thrive in a cloud-native environment, which aims to automate, centralize and comprehensively handle all forms of secrets. This is the best way to deal with the demand that cloud-native provides for efficiency, scalability, and versatility.



