The Internet of Things (IoT) is an interconnected array of electronic devices linked by the Internet, through which they transmit and receive data. The original “thing” was a Coca Cola vending machine which was able to report how many bottles of soda were left inside. But, along with the Internet, IoT has come a long way since then. It is now a widespread and growing phenomenon that is classified into two main domains: Consumer and Business.
Consumer IoT: Includes devices like refrigerators, door locks, light bulbs, surveillance systems that are a part of smart homes. Also, IoT consumer/lifestyle devices like fitness bands, smartwatches, drones, etc.
Business IoT: Segmented by its verticals to include devices like electricity, gas, water meters used by utility companies. And devices used in connected vehicles, retail, health, agriculture, etc.
Pepper IoT: Smart devices aren’t so bright when it comes to security
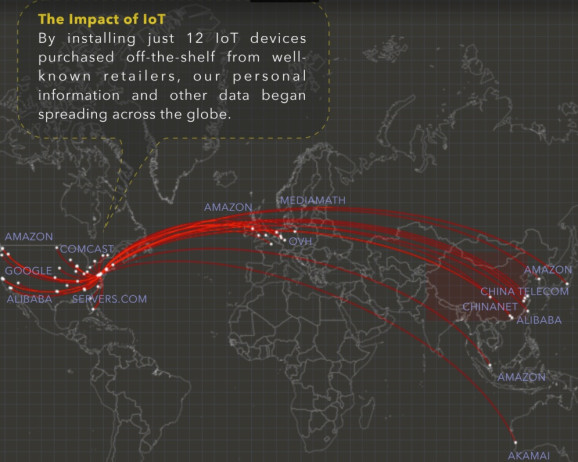
According to an analysis done by Gartner (a research and consultancy company), there will be around 21 billion connected IoT devices by 2020. And while we quote this statistic with pride and look curiously at the business opportunities it will give rise to, there is one alarming concern – IoT security. The increasing popularity of IoT has raised some serious security issues since more the number of smart devices, more is the possibility of attack vectors. The DDoS (Distributed Denial of Service) attacks, in the year 2016, that affected IoT devices around the world was an eye-opener and a proof that the security threat against IoT is real. It is imperative for digital businesses to balance the benefits that IoT-connected products can deliver with the recognition that these devices have become an attractive attack plane for cybercriminals who are seeking to cause disruption and exfiltrate sensitive data.
Just like any other emerging technology, IoT also comes with lots of benefits and risks. Many IoT devices lack some basic security requirements. There are a plethora of IoT protocols, that create security blind spots. The scope of IoT deployments hinders visibility into security incidents. There is a lack of responsibility regarding privacy and security.
Some risks associated with both home and enterprise IoT include the following:
Data security concerns
Physical safety risks
Privacy issue
Data storage management
So, what can be done to secure our IoT-connected world?
You can put some personal security measures in place to fortify your devices against the attacks by cybercriminals. And this is where IoT security comes in.
What is IoT Security?

Minimum Standards for Tackling IoT Security
In the development of an IoT application, security and testing frameworks play a very important role. IoT Security is defined as “the technology area concerned with safeguarding the connected devices and networks in the Internet of Things (IoT).” Simply put, IoT security refers to the precautionary measures taken to build the security of IoT devices and reduce their susceptibility to attacks from criminals.
Here are some IoT Security Solutions for the most common IoT security issues:
- IoT network security: Always protect and secure the network that connects IoT devices to back-end systems on the internet, by implementing traditional security features like antivirus, firewalls, and intrusion prevention and detection systems. IoT network security can be a bit challenging because there is a wider range of communication protocols, standards, and device capabilities. All of these pose significant issues and increased complexity.
- IoT authentication: Provide the ability for users to authenticate an IoT device by introducing multiple user management features for a single device (like a connected car), ranging from simple static passwords to robust authentication mechanisms like two-factor authentication and biometrics.
- IoT encryption: Encryption of data at rest and in transit between IoT edge devices and back-end systems helps to maintain data integrity and prevents data sniffing by hackers. Encryption can be done by using cryptographic algorithms and fully-encrypted key lifecycle management processes that would boost the overall security of user data and privacy.
- IoT PKI: To ensure a secure connection between an IoT device and an application, IoT public key infrastructure security methods can be used, such as X.509 digital certificate, cryptographic key, and life-cycle capabilities including public/private key generation, distribution, management, and revocation.
- IoT security analytics: Collect, aggregate, monitor, and normalize data from IoT devices and then provide actionable reporting and alerting on specific activities. These security analytics solutions are starting to add sophisticated machine learning, AI, and big data techniques to provide more predictive modeling and anomaly detection. IoT Security Analytics Solutions are capable to detect IoT-specific attacks and intrusions, which can’t even be identified by traditional network security solutions like firewalls.
- IoT API security: IoT API Security methods can be used to protect the integrity of the data movement between IoT devices, back-end systems, and applications using documented REST-based APIs. It also ensures that only authorized devices, developers, and apps are communicating with APIs or detecting any potential threats and attacks against specific APIs.
- Develop Secured IoT Apps: The developers of IoT applications need to emphasize on the security aspect of the app by strictly implementing all the above-mentioned security technologies. The developers must try their best to strike a perfect balance between the User Interface and Security of IoT apps.

Ten best practices for securing the Internet of Things in your organization
Most of these IoT security techniques revolve around two things, keeping IoT secure against attacks and keeping user-data safe, both of which can be resolved with strict legal and regulatory frameworks. The implementation of these security options will secure your IoT devices against any external security breach. And as the evolution of IoT-specific security threats will undoubtedly drive innovation in this space, you can expect more new IoT-specific security technologies emerging in the near future.
To summarize, IoT security cannot be an afterthought – it should be an integral part of the device. Rather than searching for a silver bullet that doesn’t exist, you must re-engineer, optimize and adapt current cutting edge security controls that work for the IT network for the complex embedded apps that is at the heart of Internet of Things.