It’s undeniable that over the years, the internet has brought many benefits it has been with us (It’s through the internet that you can access the information on this article)
As Lockdown and Restrictions Continue, These Are the Best Games to Pass the Time
Despite vaccines being on the way, it looks like coronavirus restrictions are going to be with us well into 2021. This could mean long days, weeks and months of being
Experiential Education Provides Deep Learning Opportunities
Experiential education can happen in the classroom through different strategies like group work, the latest tech trends, and role-playing. But then, what is experiential learning? According to Aristotle, men become
The Benefits of Making Legal Online Wills
Creating a will is one of the activities that many people know they must do, but just a few of them prioritize it. Perhaps it is the inconvenience of meeting
Tips to Choose the Best Gift for Grandparents
Whether it’s your grandparent’s birthday, anniversary, Christmas, Grandparents’ Day, or any special event in their life, you must be scrambling around choosing a perfect gift for them. What do they
Windows Users Must Follow These Rules if They Really Care About Their Data
The idea of cyber-breaches and data-stealing has become a paradoxical by-product of technological advancements. Think of it like the development of the atomic bomb during times of increasing military developments.
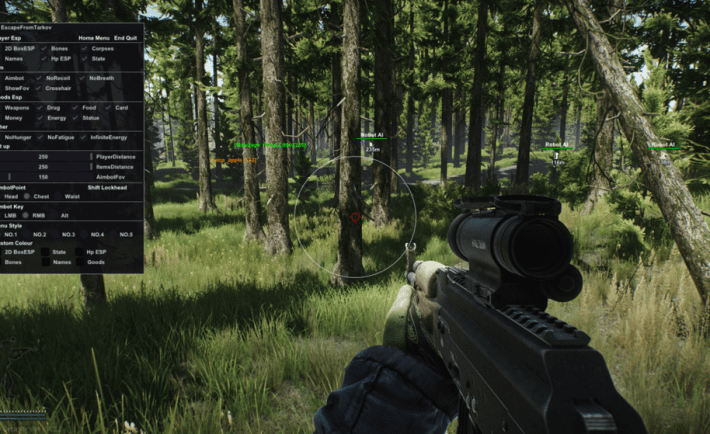
EFT Hacks: How to Stay Undetected While Using Them
Staying undetected while using hacks is particularly difficult. Even though hacks are known as enhancement software that make things easier for you, they also make it more difficult for you
Get Your Tech Products Reviewed: Submit Your Startup at Joe Tech Reviews
We know that there are tons of startups out there looking to get their products reviewed and featured online, so today we would like to highlight a service just for